In today’s digital world, protecting your devices and data from cyber threats is crucial. A firewall, acting as a guardian for your network, plays a vital role in maintaining cybersecurity. This guide will provide a comprehensive overview of how to check your firewall settings, ensuring your devices remain secure and protected.
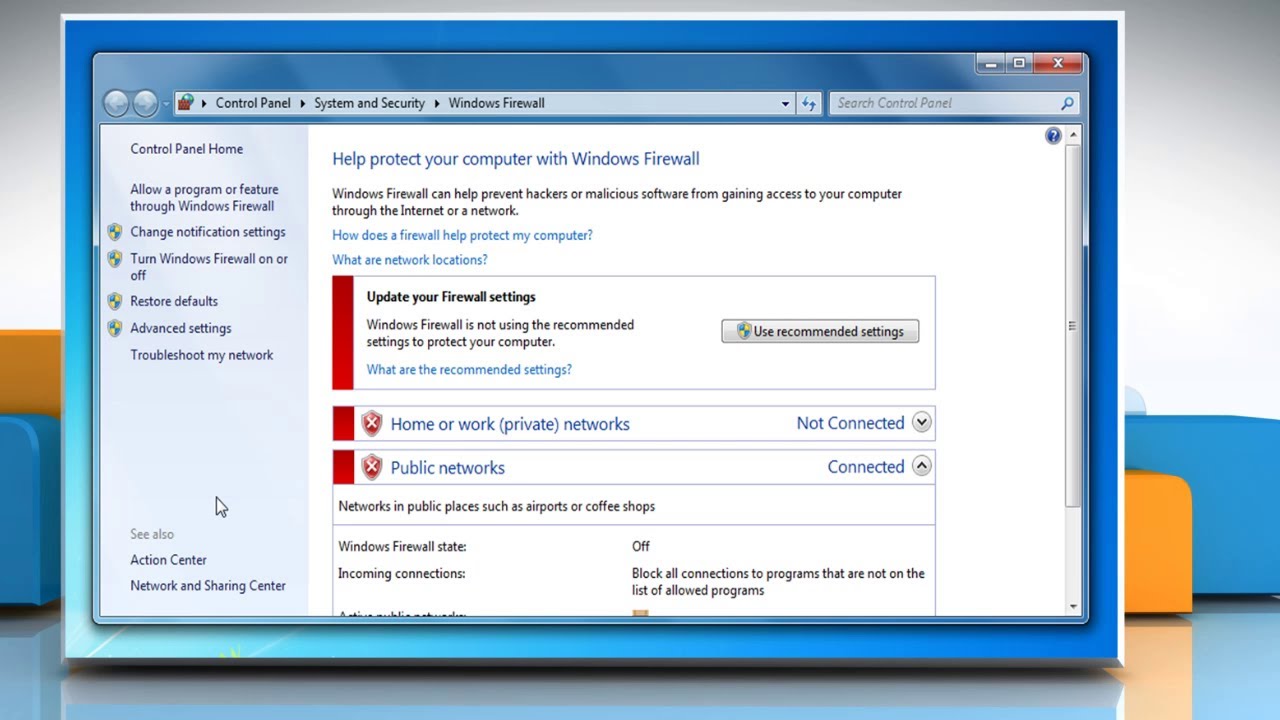
Image: tanbinger.weebly.com
Understanding Firewall Settings: A Necessity for Online Safety
A firewall is a software program or hardware device that monitors and controls incoming and outgoing network traffic. Its primary function is to block malicious traffic while allowing legitimate traffic to pass through, protecting your system from unauthorized access and potential security breaches. To ensure optimal security, it is essential to configure your firewall settings correctly and regularly check their functionality.
Checking Your Firewall Settings: A Step-by-Step Guide
Follow these steps to check your firewall settings:
- Identify Your Firewall Settings: Access the firewall settings on your computer or device. For Windows users, go to Control Panel > Windows Defender Firewall. Mac users can navigate to System Preferences > Security & Privacy > Firewall.
- Check Firewall Status: Ensure that your firewall is turned on and active. This prevents unauthorized access to your network and data.
- Review Inbound and Outbound Rules: Firewalls have rules that govern the flow of traffic. Examine these rules to ensure that only necessary connections are allowed through, minimizing potential vulnerabilities.
- Monitor Firewall Logs: Firewall logs record details of blocked traffic and detected threats. Regularly review these logs to identify potential security concerns or suspicious activity.
- Update Firewall Settings: Software updates often include security enhancements and bug fixes for firewalls. Always keep your firewall software up to date to ensure optimal performance and protection.
Expert Tips and Advice for Enhanced Firewall Security
Consider these expert tips to bolster your firewall’s effectiveness:
- Enable Stealth Mode: This feature hides your firewall from hackers, making it harder for them to target your system.
- Use Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity and alert you to potential threats.
- Consider a Hardware Firewall: External hardware firewalls provide an additional layer of protection beyond software-based firewalls.
- Periodically Test Your Firewall: Conduct regular tests to verify that your firewall is functioning correctly and effectively blocking unauthorized access.
By following these tips and expert advice, you can enhance your firewall’s security capabilities and minimize the risk of cyber threats.

Image: www.wikihow.com
FAQs on Firewall Settings: Addressing Common Concerns
- Q: How do I know if my firewall is blocking legitimate traffic?
- A: Check firewall logs for any blocked traffic that may have been legitimate.
- Q: Can firewalls prevent all cyber threats?
- A: While firewalls provide substantial protection, they are not foolproof and may require additional security measures.
- Q: How often should I update my firewall settings?
- A: Regularly update your firewall software as recommended by the vendor to ensure optimal protection against evolving threats.
How Do I Check My Firewall Settings
Conclusion: Securing Your Digital Landscape Through Firewall Vigilance
In the ever-evolving cyber landscape, a properly configured firewall serves as a vital defense mechanism. By following the steps outlined in this article, you can safeguard your network and data from unauthorized access. Remember to regularly check your firewall settings, implement expert advice, and stay informed about the latest security developments. Embrace firewall vigilance to protect your digital assets and ensure your online safety.
Do you value the information you gained from this article? Let us know in the comments below.


/GettyImages-1303637-two-way-mirror-57126b585f9b588cc2ed8a7b-5b8ef296c9e77c0050809a9a.jpg?w=740&resize=740,414&ssl=1)


